Introduction to JTAG Chains
JTAG (Joint Test Action Group) is a standard interface used for testing, debugging, and programming electronic devices. It provides a way to access and control the internal components of a system, such as microprocessors, FPGAs, and memories. JTAG chains are formed when multiple JTAG-compliant devices are connected together in a daisy-chain configuration, allowing them to be accessed and controlled through a single JTAG interface.
What is JTAG?
JTAG, formally known as IEEE 1149.1 Standard Test Access Port and Boundary-Scan Architecture, is a standard that defines a method for testing and debugging printed circuit boards (PCBs) and integrated circuits (ICs). It was developed by the Joint Test Action Group, a consortium of electronics companies, to address the challenges of testing increasingly complex electronic systems.
The JTAG standard defines a set of hardware and software protocols that enable external access to the internal components of a system. It provides a way to perform boundary-scan testing, which involves testing the interconnections between ICs on a PCB, as well as internal testing of the ICs themselves.
JTAG Architecture
The JTAG architecture consists of several key components:
- Test Access Port (TAP): The TAP is a four-wire interface that provides access to the JTAG functionality of a device. It consists of the following signals:
- Test Clock (TCK): Provides the clock signal for the JTAG operations.
- Test Mode Select (TMS): Controls the state of the TAP controller.
- Test Data Input (TDI): Serves as the serial input for JTAG data and instructions.
-
Test Data Output (TDO): Serves as the serial output for JTAG data and instructions.
-
TAP Controller: The TAP controller is a state machine that controls the operation of the JTAG interface. It responds to the signals on the TAP and generates the appropriate control signals for the other JTAG components.
-
Instruction Register (IR): The IR holds the current JTAG instruction being executed. It is loaded with instructions through the TDI signal and can be read through the TDO signal.
-
Data Registers (DRs): DRs are used to store and shift data during JTAG operations. There are several types of DRs, including the Boundary Scan Register (BSR), which is used for boundary-scan testing, and the BYPASS register, which is used to bypass a device in a JTAG chain.
Benefits of JTAG
JTAG provides several benefits for testing and debugging electronic systems:
-
Standardized Interface: JTAG provides a standardized interface for accessing and controlling the internal components of a system, regardless of the specific device or manufacturer.
-
Boundary-Scan Testing: JTAG enables boundary-scan testing, which allows testing the interconnections between ICs on a PCB without the need for physical test probes.
-
In-System Programming (ISP): JTAG can be used for in-system programming of devices such as FPGAs and microcontrollers, eliminating the need for external programming hardware.
-
Debug and Trace Capabilities: JTAG provides debug and trace capabilities, allowing developers to monitor and control the execution of software on a system.
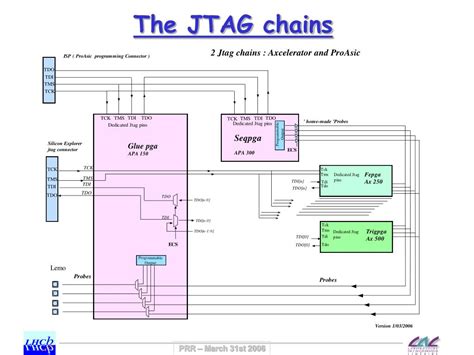
JTAG Chain Configuration
A JTAG chain is formed when multiple JTAG-compliant devices are connected together in a daisy-chain configuration. Each device in the chain has its own TAP, and the TDO of one device is connected to the TDI of the next device in the chain. The TMS and TCK signals are shared among all devices in the chain.
Connecting Devices in a JTAG Chain
To create a JTAG chain, the devices are connected as follows:
- The TDI of the first device in the chain is connected to the JTAG interface’s TDI signal.
- The TDO of each device is connected to the TDI of the next device in the chain.
- The TDO of the last device in the chain is connected to the JTAG interface’s TDO signal.
- The TMS and TCK signals are connected to all devices in the chain in parallel.
Here’s an example of a JTAG chain configuration:
JTAG Interface -- TDI --> [Device 1] -- TDO --> [Device 2] -- TDO --> [Device 3] -- TDO --> JTAG Interface
TCK ---------------------------------------------------------->
TMS ---------------------------------------------------------->
Accessing Devices in a JTAG Chain
To access a specific device in a JTAG chain, the JTAG instructions and data must be shifted through the chain until they reach the target device. The process involves the following steps:
- The JTAG instruction is shifted into the IR of all devices in the chain through the TDI signal.
- The JTAG data is shifted into the appropriate DR of the target device through the TDI signal.
- The JTAG data is shifted out of the DR of the target device through the TDO signal and through the TDI/TDO connections of the subsequent devices in the chain.
The length of the JTAG chain affects the time required to access a specific device, as the instructions and data must be shifted through all the devices in the chain.
JTAG Chain Configuration Examples
Here are a few examples of JTAG chain configurations:
- Single Device Chain:
JTAG Interface -- TDI --> [Device] -- TDO --> JTAG Interface
TCK ---------------------->
TMS ---------------------->
- Multiple Device Chain:
JTAG Interface -- TDI --> [Device 1] -- TDO --> [Device 2] -- TDO --> [Device 3] -- TDO --> JTAG Interface
TCK ---------------------------------------------------------------->
TMS ---------------------------------------------------------------->
- Mixed Device Chain:
JTAG Interface -- TDI --> [CPU] -- TDO --> [FPGA] -- TDO --> [Memory] -- TDO --> JTAG Interface
TCK -------------------------------------------------------------->
TMS -------------------------------------------------------------->

JTAG Chain Management
Managing JTAG chains involves several considerations, such as chain length, device compatibility, and signal integrity. Proper management ensures reliable operation and efficient access to the devices in the chain.
JTAG Chain Length Considerations
The length of a JTAG chain can have an impact on the performance and reliability of the JTAG operations. As the chain length increases, several factors come into play:
-
Signal Integrity: Longer JTAG chains can lead to signal degradation due to increased capacitance and resistance. This can result in slower operating speeds and potential signal integrity issues.
-
Access Time: The time required to access a specific device in the chain increases with the chain length, as the instructions and data must be shifted through all the devices in the chain.
-
Power Consumption: Each device in the chain contributes to the overall power consumption of the JTAG interface. Longer chains may require careful power management to ensure proper operation.
To mitigate these issues, designers may need to consider using JTAG chain extenders, buffers, or repeaters to maintain signal integrity and performance in longer chains.
Device Compatibility in JTAG Chains
When creating a JTAG chain, it is important to ensure compatibility among the devices in the chain. Compatibility considerations include:
-
JTAG Standard Compliance: All devices in the chain must comply with the JTAG standard (IEEE 1149.1) to ensure proper communication and operation.
-
Voltage Levels: The devices in the chain must operate at compatible voltage levels to avoid damage or malfunction. Level shifters may be required if devices with different voltage levels are used in the same chain.
-
Instruction and Data Register Lengths: The length of the IRs and DRs of the devices in the chain should be taken into account when designing the JTAG interface and software.
Signal Integrity in JTAG Chains
Maintaining signal integrity is crucial for reliable JTAG operation. Several factors can impact signal integrity in a JTAG chain:
-
Trace Length and Routing: Long PCB traces and improper routing can introduce signal reflections, crosstalk, and noise, which can degrade JTAG signal quality. Proper PCB design techniques, such as controlled impedance traces and appropriate terminations, can help minimize these issues.
-
Signal Termination: Proper termination of JTAG signals is essential to minimize reflections and maintain signal integrity. Techniques such as series termination resistors or pull-up/pull-down resistors can be used depending on the specific requirements of the system.
-
Shielding and Grounding: Adequate shielding and proper grounding techniques can help reduce noise and interference in JTAG signals. This may involve using shielded cables, ground planes, or dedicated JTAG ground pins.
JTAG Chain Testing and Debugging
Testing and debugging JTAG chains is an important part of the development and manufacturing process. Several techniques can be used to verify the integrity and functionality of a JTAG chain:
-
Boundary-Scan Testing: Boundary-scan testing can be used to verify the interconnections between devices in the chain. This involves shifting test patterns into the BSRs of the devices and comparing the captured results with expected values.
-
Chain Integrity Testing: Chain integrity testing involves verifying the continuity and connectivity of the JTAG chain. This can be done by shifting known patterns through the chain and checking the output for expected values.
-
Device Identification: JTAG devices typically have an IDCODE register that contains information about the manufacturer, part number, and version of the device. Reading the IDCODE of each device in the chain can help verify the presence and correct placement of devices.
-
Debugging with JTAG: JTAG can be used for debugging hardware and software issues in the system. This may involve using JTAG-based debuggers, trace tools, or in-circuit emulators to monitor and control the execution of code on the target devices.

JTAG Chain Configuration and Management Tools
Several tools and techniques are available to assist in configuring and managing JTAG chains. These tools help simplify the process of designing, testing, and debugging JTAG-based systems.
JTAG Chain Configuration Tools
JTAG chain configuration tools help designers create and manage JTAG chains by providing a graphical or text-based interface for specifying the devices in the chain and their connections. Some popular JTAG chain configuration tools include:
-
Xilinx iMPACT: A tool provided by Xilinx for configuring and programming Xilinx FPGAs and CPLDs in a JTAG chain.
-
Altera Quartus II: A tool provided by Altera (now part of Intel) for configuring and programming Altera FPGAs and CPLDs in a JTAG chain.
-
OpenOCD: An open-source tool that supports various JTAG adapters and provides a command-line interface for configuring and managing JTAG chains.
These tools typically allow designers to specify the devices in the chain, their order, and the connections between them. They may also provide features such as automatic chain detection, device identification, and boundary-scan testing.
JTAG Chain Management Tools
JTAG chain management tools help developers and engineers manage and control JTAG chains during testing, debugging, and programming. Some popular JTAG chain management tools include:
-
SEGGER J-Link: A family of JTAG adapters and software tools that support a wide range of microcontrollers and FPGAs. J-Link provides features such as debugging, tracing, and flash programming.
-
FTDI FT2232H: A USB-to-JTAG adapter that supports various JTAG chains and provides a multi-purpose interface for debugging and programming.
-
Texas Instruments XDS: A series of JTAG adapters and software tools specifically designed for TI’s microcontrollers and processors.
These tools typically provide a user-friendly interface for controlling the JTAG chain, setting breakpoints, inspecting memory and registers, and performing other debugging tasks.
Boundary-Scan Testing Tools
Boundary-scan testing tools are used to verify the interconnections between devices in a JTAG chain and to test the functionality of the individual devices. Some popular boundary-scan testing tools include:
-
JTAG Technologies ProVision: A comprehensive boundary-scan testing tool that supports various JTAG standards and provides features such as automatic test generation, fault coverage analysis, and pin-level diagnostics.
-
Goepel Electronic CASCON: A boundary-scan testing tool that offers a graphical interface for creating and executing test plans, as well as support for mixed-signal testing and in-system programming.
-
XJTAG: A boundary-scan testing solution that provides a high-level programming language for describing tests, as well as integration with popular design tools and hardware debuggers.
These tools help designers and test engineers create and execute boundary-scan tests, analyze results, and diagnose faults in the JTAG chain.
Frequently Asked Questions (FAQ)
-
What is the purpose of a JTAG chain?
A JTAG chain allows multiple JTAG-compliant devices to be connected together and accessed through a single JTAG interface. It enables testing, debugging, and programming of the devices in the chain using a standardized interface and protocol. -
How many devices can be connected in a JTAG chain?
Theoretically, there is no limit to the number of devices that can be connected in a JTAG chain. However, practical limitations such as signal integrity, access time, and power consumption may restrict the maximum number of devices in a chain. The specific limit depends on factors such as the JTAG interface, device characteristics, and PCB design. -
Can devices with different JTAG interfaces be used in the same chain?
Yes, devices with different JTAG interfaces can be used in the same chain as long as they comply with the JTAG standard (IEEE 1149.1). However, care must be taken to ensure compatibility in terms of voltage levels, instruction and data register lengths, and other parameters. -
What happens if a device in the JTAG chain is not functioning properly?
If a device in the JTAG chain is not functioning properly, it can affect the operation of the entire chain. Depending on the nature of the fault, it may prevent access to devices beyond the faulty device or cause incorrect data to be shifted through the chain. In such cases, chain integrity testing and boundary-scan testing can be used to isolate the faulty device and diagnose the issue. -
Can JTAG chains be used for production testing?
Yes, JTAG chains are commonly used for production testing of electronic assemblies. Boundary-scan testing, enabled by JTAG, allows for efficient testing of interconnections between devices and can help identify manufacturing defects such as shorts, opens, and misaligned components. JTAG-based testing can be automated and integrated into the production test process, reducing test time and improving fault coverage.
Conclusion
JTAG chains are a powerful tool for testing, debugging, and programming electronic systems. By connecting multiple JTAG-compliant devices in a daisy-chain configuration, designers and engineers can access and control the internal components of a system through a single JTAG interface. However, managing JTAG chains requires careful consideration of factors such as chain length, device compatibility, and signal integrity.
Various tools and techniques are available to assist in configuring and managing JTAG chains, including chain configuration tools, management tools, and boundary-scan testing tools. These tools help simplify the process of designing, testing, and debugging JTAG-based systems, enabling faster development and more reliable operation.
As electronic systems continue to increase in complexity, the use of JTAG chains and associated tools will remain an essential part of the development and manufacturing process. By understanding the principles and best practices of JTAG chain management, designers and engineers can effectively leverage this powerful technology to create robust and reliable electronic products.
No responses yet